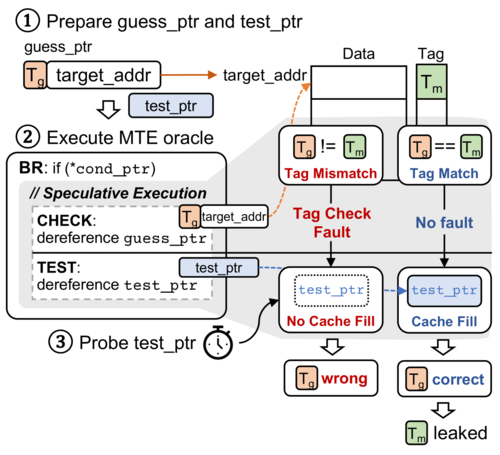
A team of researchers from Seoul University and Samsung developed an attack technique on ARM processors, codenamed TikTag, which can be used to bypass the hardware MemTag protection mechanism (MTE, Memory Tagging Extension), present in chips based on the ARMv8.5-A architecture. The attack allows the contents of TikTags to be determined for arbitrary memory addresses due to data leaks resulting from speculative execution of CPU instructions.
MemTag technology makes it possible to bind tags to areas in memory and organize checking the correct use of pointers to block the exploitation of vulnerabilities caused by accessing already freed memory blocks, buffer overflow and access before initialization. When using MemTag, a 4-bit tag is created for every 16 bytes of physical memory, which acts as a kind of key to access this memory. The tag can be generated by the application for the allocated memory area using special CPU instructions, and then stored in the top unused bits of the pointer. When accessing memory using a tagged pointer, the processor checks that the tag bound to the pointer matches the tags bound to the memory blocks, and allows access only if the tags match.
Advertisement
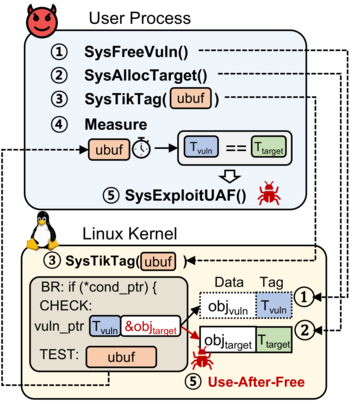
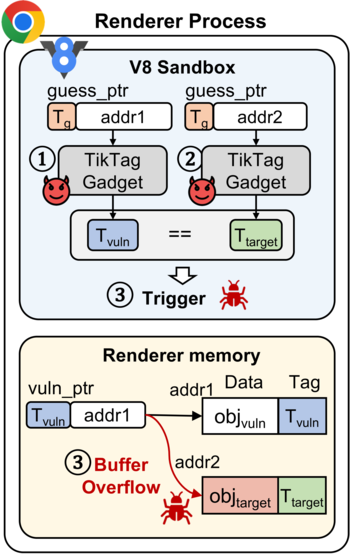
The proposed attack method makes it possible to identify tags associated with memory blocks and bypass MemTag protection. Researchers have demonstrated the possibility of carrying out a TikTag attack by exploiting vulnerabilities in the Linux kernel and the Chrome browser, using instruction sequences (gadgets) existing in these products, leading to speculative code execution. Such gadgets, when executed in speculative mode by code that operates on pointers, cause MemTag metadata to be read depending on external conditions that can be influenced by the attacker. Once an incorrect prediction is determined, the result of the speculative execution is discarded, but the resulting data remains in the cache and can then be retrieved using side-channel analysis. The probability of successfully bypassing MemTag protection in the tests carried out was estimated at 95% when carrying out an attack within approximately 4 seconds.
Two types of gadgets have been identified that leak information about MemTags. In the first case, speculative execution occurs when a branch is mispredicted, and the conditions for gadget execution can be created through system call manipulation. In the second case, speculative execution occurs due to an error in predicting the relationship between reads and writes when using STLF (Store-To-Load-Forwarding) optimization, which allows you to select a tag by judging the state of the cache (if the tag matches, the value will be directly forwarded from the previous command “store” into a “load” operation and will change the state of the cache). The first type of gadget is suitable for attacking the Linux kernel, and the second is suitable for attacking the V8 JavaScript engine used in Chromium-based browsers. Prototype toolkit for carrying out an attack published on GitHub.
Advertisement
ARM has confirmed that the attack can be carried out on systems with Cortex-X2, Cortex-X3, Cortex-A510, Cortex-A520, Cortex-A710, Cortex-A715 and Cortex-A720 processors, but I don't intend to make changes to the CPU to block the problem, since the MemTag architecture means that tags are not secret data for applications. The issue also remains unfixed in the Chromium codebase, as MemTag-based protection is not yet applied by default in the Chrome browser. The team responsible for the security of the Android platform acknowledged the possibility of an attack on Pixel 8 devices that use MemTag protection, added patches to block leaks, and expressed their willingness to pay a reward for the vulnerability found.
As workarounds to block the attack, researchers suggest using sb or isb instructions to disable speculative execution during critical memory operations, or including padding from other instructions between branch instructions and memory access instructions.
Thanks for reading: