After 8 months of development presented significant release of a dedicated browser Tor Browser 13.5, which continues to develop functionality based on the ESR branch of Firefox 115. The browser is focused on ensuring anonymity, security and privacy, all traffic is redirected only through the Tor network. It is impossible to contact directly through the standard network connection of the current system, which does not allow tracking the user’s real IP address (if the browser is hacked, attackers can gain access to system network parameters, so products such as Whonix should be used to completely block possible leaks). Tor Browser builds prepared for Linux, Android, Windows and macOS.
To provide additional security, Tor Browser includes the “HTTPS Only” setting, which allows you to use traffic encryption on all sites where possible. An add-on is included to reduce the threat of JavaScript attacks and block plugins by default NoScript. To combat blocking and traffic inspection, they use fteproxy And obfs4proxy. To organize an encrypted communication channel in environments that block any traffic other than HTTP, alternative transports are proposed.
Advertisement
To protect against user movement tracking and visitor-specific features, the WebGL, WebGL2, WebAudio, Social, SpeechSynthesis, Touch, AudioContext, HTMLMediaElement, Mediastream, Canvas, SharedWorker, WebAudio, Permissions, MediaDevices.enumerateDevices, and screen APIs are disabled or limited. orientation, and also disabled telemetry sending tools, Pocket, Reader View, HTTP Alternative-Services, MozTCPSocket, “link rel=preconnect”, modified libmdns.
In the new version:
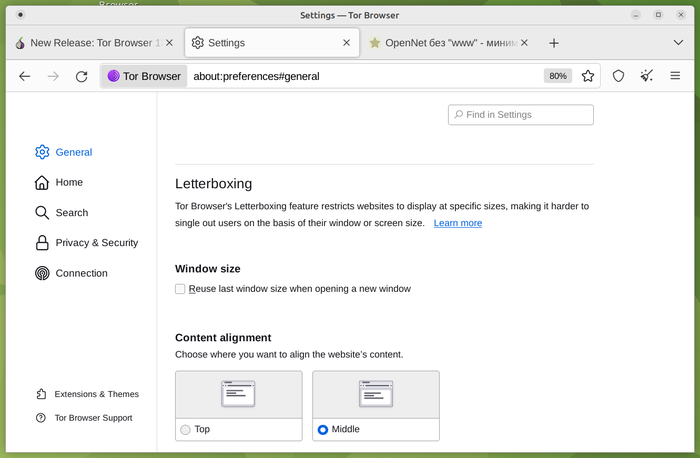
- The “letterboxing” mechanism has been modernized, adding padding around the content of web pages to prevent leakage of information about the size of the screen and the open window. The appearance of a gray border around the content was perceived by some users as a problem with the rendering of the site or a bug in the browser. To make the empty space around the page seem like a deliberate change rather than a content display issue, the new version adds a thin border with rounded corners. When you double-click on a frame, the Tor Browser window now automatically resizes to the selected letterboxing size and the frame is completely hidden.
A separate section has been added to the configurator to configure “letterboxing” options, such as keeping the same size when opening a new window and aligning content to the center or top border.
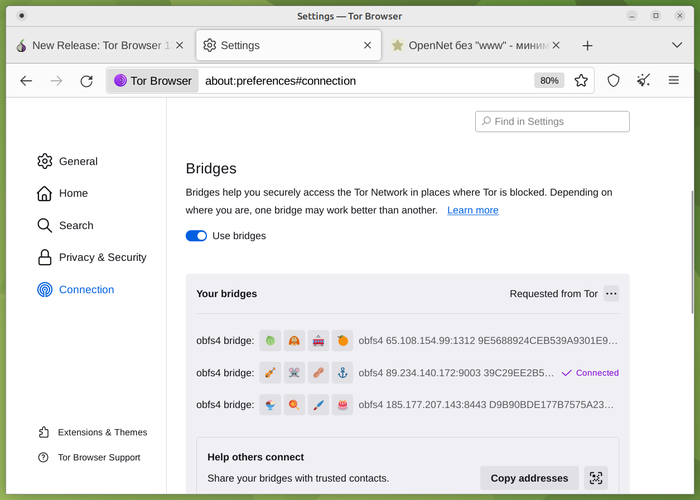
- In the bridge node configuration interface, the search for working bridge nodes has been improved and the management of several bridge nodes at once has been simplified. The design of information cards with bridge node data has been changed, with which you can save working bridges and exchange them with other users. Instead of displaying cards as a stack, the new version implements a compact list in which cards are separated based on the source of addition (built-in, manually added by the user, or requested from Tor).
When using three or fewer bridge nodes, it is possible to share them with other users at once via a QR code, without separately transmitting information about each node. A “Find more bridges” section has been added, which lists additional ways to obtain information about bridge nodes, such as a telegram channel, a separate website, and an email request.
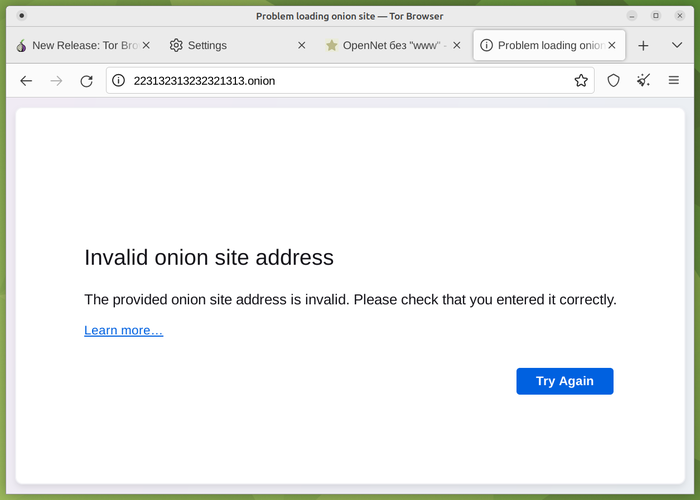
- Messages about errors that occur when working with onion sites, for example, typos when writing an address or network failures, have been simplified. Pages with similar errors for onion sites are brought to the style of error messages that arise when working with regular sites.
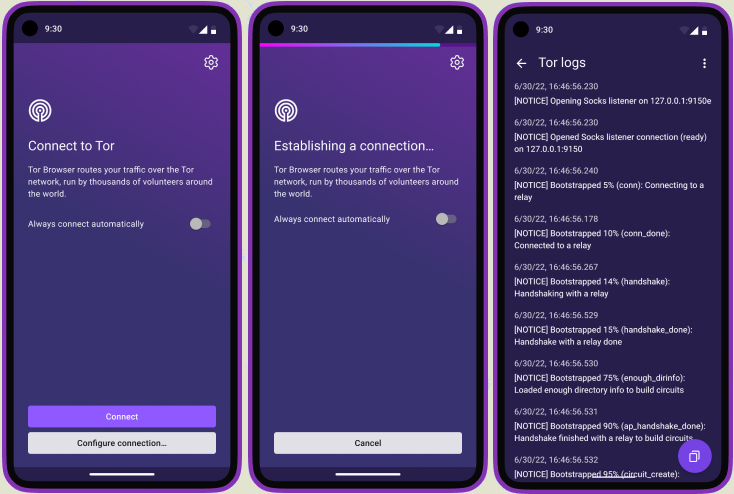
- In the version for the Android platform, the interface displayed when connecting to the Tor network has been completely changed, which is closer to the Tor Browser interface for desktops. Added a button that allows you to gain full access to settings before the connection to Tor is completed. It is noted that the change in the connection interface was the first step towards the future implementation in the Android version of the Connection Assist component, which automates the search and selection of bridge nodes and alternative transport in situations where a direct connection could not be established.
- The Android version has expanded tools for viewing the operation log, which reflects activity when connecting to Tor, as well as errors or warnings that arise during interaction with the network. The information added to the log does not contain sensitive data, such as sites opened, but can be useful for diagnosing problems. If previously the log could only be viewed before the connection was established using a screen gesture that shifted to the right, now it can be accessed during work from the connection settings section. In addition, a button for copying content to the clipboard has been added to the log viewing interface.
Thanks for reading: