The P2P botnet P2PInfect has resumed activity and is now deploying a ransomware module and a cryptocurrency miner on the attacked Redis servers.
According to the company Cado Security, which has been monitoring P2PInfect for some time, it appears the malware is now operating as a botnet for hire, although researchers are not entirely sure. It is unclear whether P2PInfect is rented out to multiple hacking groups or is operated by a single team of attackers.
Advertisement
Let us recall that P2PInfect was first noticed in the summer of 2023 by experts at Palo Alto Networks Unit 42. At that time it was reported that the malware was aimed at Redis servers that were vulnerable to the problem CVE-2022-0543which allows you to escape from the sandbox, as well as execute arbitrary code.
From August to September 2023, P2PInfect steadily increased in activity and carried out thousands of attack attempts each week, and also acquired new features such as cron-based sticky mechanisms and redundant communication systems.
However, P2PInfect did not perform any malicious actions on the compromised devices, so its goals remained unclear.
In December 2023, analysts discovered a new variant of P2PInfect designed to attack 32-bit MIPS (Microprocessor without Interlocked Pipelined Stages) processors used in routers and IoT devices.
Advertisement
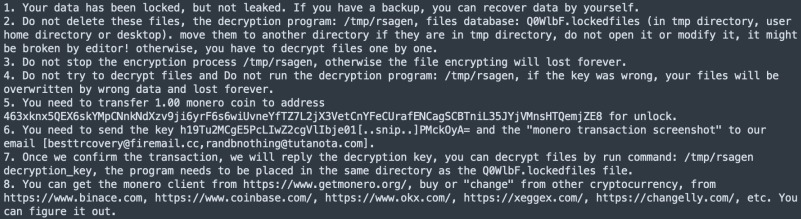
As Cado Security now reports, starting May 16, 2024, devices infected with P2PInfect are commanded to download and run a ransomware payload (rsagen) from a specified URL, with the command remaining in effect until December 17, 2024.
Once launched, the ransomware binary searches the system for a ransom note (“Your data has been locked!.txt”) to avoid re-encrypting already compromised systems.
The ransomware itself targets files with specific extensions, including databases (SQL, SQLITE3, DB), documents (DOC, XLS) and media files (MP3, WAV, MKV). It adds the .encrypted extension to the resulting files. The malware goes through all directories, encrypts data and saves a database of encrypted files in a temporary file with the .lockedfiles extension.
Additionally, the XMR (Monero) miner, dormant in previous versions, is now activated, placed in a temporary directory, and launched five minutes after the main payload has launched.
Judging by the malware samples studied by experts, so far P2PInfect operators have earned 71 XMR, that is, about $10,000 at the current exchange rate. But there is a high probability that hackers are using other wallets that experts have not yet discovered.
It is noted that the miner in the new P2PInfect is configured in such a way as to use all the available computing power of the infected machine, which often makes it difficult for the ransomware module to work.
The researchers also identify a new rootkit that allows P2PInfect bots to hide their malicious processes and files from security tools by using multiple processes at once to disguise themselves. While a rootkit is theoretically capable of hiding file operations, data access events, and network connections, its effectiveness is often limited by in-memory Redis deployments.
Experts conclude that P2PInfect is no longer someone's experiment, but a real threat to Redis servers, capable of destroying data and seizing computing power for profit.
